Implementation of Risk and Security management
Know the possible risks and security threats associated with the functioning of your organization, eliminate their occurrence and prepare for them by planning an appropriate response.
Key challenges
implemented projects end in failure
there is no appropriate response to incoming risks
there is an increase in costs associated with the implementation of the project
security breaches occur causing extensive damage
Achieved goals
time savings
financial cost savings
mitigation of security threat risks
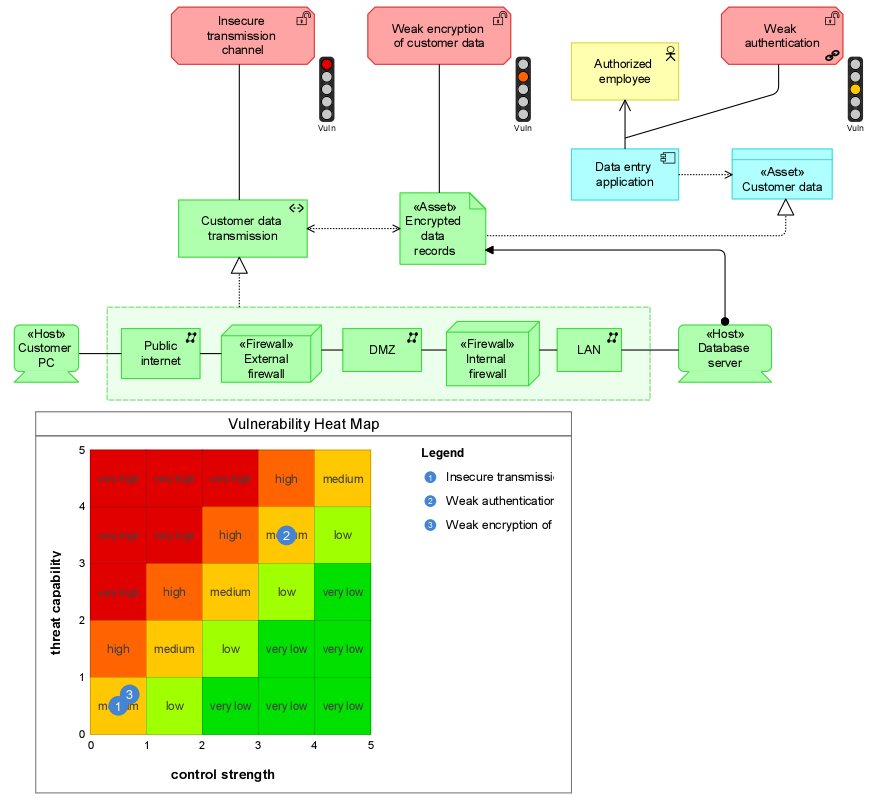
Detection, analysis and elimination of risks and security threats is one of the basic pillars of successfully implemented projects, but also the operation of the organization and its information systems (aspects of CIA - confidentiality, integrity and availability). The absence of possible risks and threats causes the implemented projects to fail, there is no adequate response to the incoming risks, there is an increase in the costs associated with the implementation of the project, there are security breaches causing extensive damage.
The digital twin of organization preserves the organization's representation in a number of disciplines, including the operating model, business processes, business strategies, data, and more. Thanks to objectification and subsequent digitization, it is possible to store information about risks, vulnerabilities, control measures, or any other objects of risk management of the security architecture. In addition, it is possible to connect directly with the operating model and evaluate it in the form of clear sets of temperatures and temperature maps.